Ethical issues with penetration testing
We have been training Information Security and IT Professionals since with a diverse lineup of relevant training courses. What we have here is a failure to communicate. As a result, penetration testing is now a widely recognised aspect of security, with the aforementioned CSI survey revealing that some 34 per cent of respondents used external services to evaluate their systems, while 41 per cent claimed to conduct such activities internally. Tens of thousands of dollars of legal bills later, a jury acquitted Puffer in all of 15 minutes. Masserini John Pescatore Larry Whiteside Jr. Venue and Jurisdiction Another key issue in pen test contracts is to determine where the pen test is being conducted.


An introduction to penetration testing and its legal implications for VARs and consultants



An introduction to penetration testing and its legal implications for VARs and consultants
The professional issues of ethical hacking include possible ineffective performance on the job. Indeed, the idea of pen testing is somewhat more worrisome in the poacher-turned-gamekeeper scenario of ex-hackers offering their services to test and secure systems, and we need to be fairly sure that anyone being taught the techniques has a properly aligned moral compass and is not going to go running off to use them inappropriately. We use cookies to provide and improve our services. Penetration testing is a specific term and focuses only on discovering the vulnerabilities, risks, and target environment with the purpose of securing and taking control of the system.



What is ethical hacking?
Public Domain Hacking significantly affects the development of systems and networks. Writing is my passion This is the first article in a six-part tutorial for consultants and value-added resellers VARs about penetration Since penetration techniques are used to protect from threats, the potential attackers are also swiftly becoming more and more sophisticated and inventing new weak points in the current applications. The ethical hacker could be at legal risk if proper care and precaution are not seriously taken.



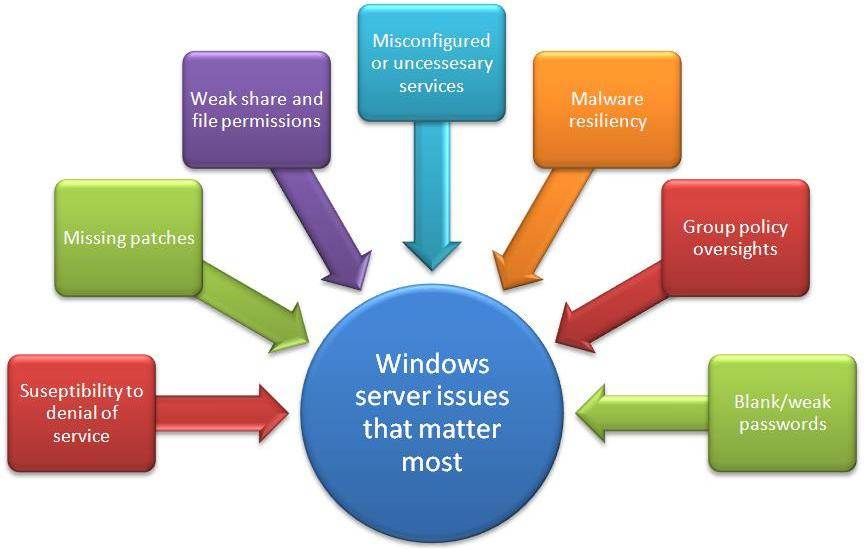

Clean system Ensure you use a clean version of your system and tools e. Before beginning a pen test, the parties should enter into a contract indicating exactly what the pen testers will do and will not do and the range of IP addresses, subnets, computers, networks or devices that will be the subject of the pen test. Remember, it is as important to document the lack of findings as it is to document the findings themselves. You do not want to get into trouble for hacking when you are conducting a test for legitimate reasons. For example on a site where user-generated content is allowed, how do you know that the person who created the page has authority to make that decision? So at the very least, follow the guidelines, but in addition, log everything you do just in case something bad happens and you need to prove it wasn't you, or wasn't deliberate!

706
82
















It seems a little bit more effective than the others, mostly because the point was not to say STAY ABSTINENT FOREVER but instead show how fast something can spread if you don't use protection, but I'm still not sure I like it as an analogy.В
tiny dick, my god !
that is not a threesome
good
kiss you pussy owo ohhhhhhhhhh
I don't understand how to answer these questions as a trans person. I didn't always identify as male so should I say that dating men was the other sex? or Same sex because you could argue I was also male and just didn't know it? lol SO CONFUSING.